Rank: Left for not the scale of repair flaw, right for not of repair " crucial " with " Gao Wei " the rate of flaw
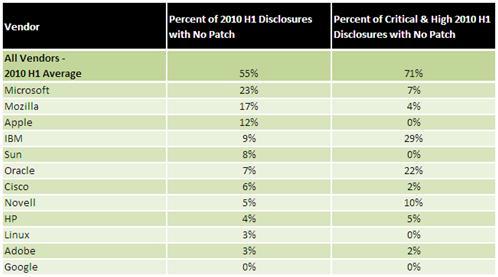
B the most popular usb harddrive enclosure eijing time on September 1 moto gp xbox best buy before dawn message, according to foreign media coverage, 3 IBM safety stud the best selling ata pci ies the group announced each old software firm to be opposite last week the report of the circumstance of safe flaw rehabilitate of oneself software, had a rank to its.
15 pin vgaThe rank shows, there is 29% in IBM oneself software " crucial " and " Gao Wei " flaw not by repair, the performance in be each old software firm is the poorest. And Gu Ge is in each rank all behave best, the flaw that accomplished all publicity (include key and tall danger hole) have seasonable patch repair.
This report is released every year twice, basically track each flaw of old software inside half an year and hacker to use flaw to launch the case of attack, firm of old to each software is foregone at the same time of flaw repair a circumstance to undertake investigate and be rankinged, be checked by tone the elephant includes Microsoft, apple, inscriptions on bones or tortoise shells of the Shang Dynasty, Cisco and him IBM t ata pci controller o wait.
north face shirtsInvestigate discovery, the foregone software flaw that Microsoft had 23% first half of the year 2010 not by repair, first what rank each old software most popular selling ata pci firm, after close therewith is to seek wisdom (of Mozilla) 17% , of the apple 12% , of IBM 9% 8% with Sun.
Be in foregone " crucial " and " Gao Wei " flaw not by the scale of repair respect, this number is as high as IBM first half of the year 29% , the rank is highest, after close therewith is inscriptio usb harddrive enclosure best buy ns on bones or tortoise shells of the Shang Dynasty 22% , of Novell 10% moto gp xbox , of Microsoft 7% 5% with HP.
However, the loophole that here crime of not divisional network exploits IBM in investigation and the flaw that discover by safe researcher. In fact, the flaw majority of statistic of the place in this investigation is by so called " white hat " the hacker discovers, they won't use flaw to have charge, and can make software becomes more safe only.
According to saying, this kind of findings report often can urge the foregone flaw in software of oneself of rehabilitate of each old s most popular selling usb harddrive enclosure oftwar ata pci best buy e firm, promote the security of software thereby. (Zhang He)
No comments:
Post a Comment